Multi-factor authentication is a process where a user is prompted during the sign-in process for an additional form of identification, such as to enter a code on their cellphone or to provide a fingerprint scan.
If you only use a password to authenticate a user, it leaves an insecure vector for attack. If the password is weak or has been exposed elsewhere, is it really the user signing in with the username and password, or is it an attacker? When you require a second form of authentication, security is increased as this additional factor isn’t something that’s easy for an attacker to obtain or duplicate.
Starting October 2019, every new Office 365 for business or Microsoft 365 Business subscription will automatically have security defaults turned on. This means that every user will have to set up MFA and install the Microsoft Authenticator app on their mobile device.
This poses a challenge when you are calling Office 365 API programatically. If a software program for e.g. WebService is running as a background thread it cannot do a MFA easily. So MFA needs to be bypassed.
The recommended approach of achieving this by using OAuth2 for SharePoint API which I had covered in one of my prior blog posts.
However there might be cases due to internal policies, where you still want to use a username/password combination for service account. This can be achieved using the steps described below.
Step 1: After multi factor authentication is enabled for user, when user tries to log in to https://portal.office.com by providing username as password, they will an option to setup multi factor authentication.
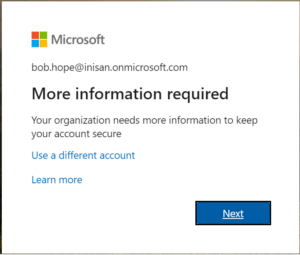
Step 2: Click on Next button to setup multi factor authentication.
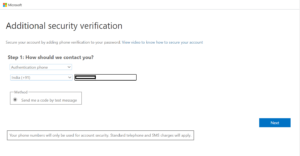
Step 3: Enter the code and click on Verify.
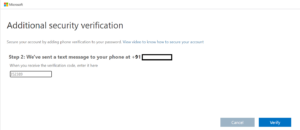
Step 4: After verifying the code, it will take to a page where it will show the app password. Copy the app password and click on Done.
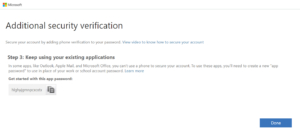
User can also manage app passwords by logging into https://portal.office.com and clicking on the username from top right pane -> My Account -> Security and Privacy -> Create and manage app passwords.
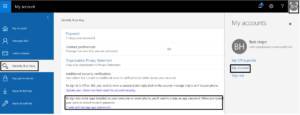
If multi factor authentication is enabled, then while creating SharePoint access tokens in AgilePoint portal, user must provide app password in the password field instead of his regular password.
Steps to create SharePoint Access Token in AgilePoint Portal.
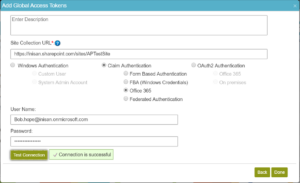
Login to AgilePoint Portal, navigate to Manage -> App Builder -> Global Access Tokens and click on Add Token button. On Add Global Access Tokens Screen, select SharePoint and click on Next
Enter Token Name, SharePoint Site collection URL, and select Office 365 radio button Claims Authentication, and then provide user name and app password and click on Validate.
Therefore you could use a username/app password combination or OAuth2 to bypass MFA for Office 365 API. However OAuth2 is a preferred approach as that will not involve any user account or password.
